1.1 找到ingress
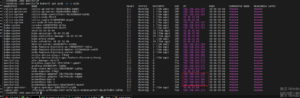
[root@TOS-1566 monitor]# iptables-save | grep prometheus-k8s
-A cali-pi-_NEUmkCPcORE5wvFnfMr -p tcp -m comment --comment "cali:CjW10JzfBGI--RdM" -m comment --comment "Policy monitoring/knp.default.prometheus-k8s ingress" -m set --match-set cali40s:Y_WAIFZXBK4GNGes7ttP63u src -m multiport --dports 8080,9090 -j MARK --set-xmark 0x10000/0x10000
-A cali-po-_NEUmkCPcORE5wvFnfMr -m comment --comment "cali:YB6FnlLkyKmL1cND" -m comment --comment "Policy monitoring/knp.default.prometheus-k8s egress" -j MARK --set-xmark 0x10000/0x10000
-A cali-pri-_Spu4GxnDUkawOUpqkv -m comment --comment "cali:QP58P71Qqj8m14Uh" -m comment --comment "Profile ksa.monitoring.prometheus-k8s ingress"
-A cali-pro-_Spu4GxnDUkawOUpqkv -m comment --comment "cali:DARrwrikWkgQvrL1" -m comment --comment "Profile ksa.monitoring.prometheus-k8s egress"
-A KUBE-EXT-IFO32E4YIRUTZPGJ -m comment --comment "masquerade traffic for monitoring/prometheus-k8s:web external destinations" -j KUBE-MARK-MASQ
-A KUBE-NODEPORTS -p tcp -m comment --comment "monitoring/prometheus-k8s:web" -m tcp --dport 31093 -j KUBE-EXT-IFO32E4YIRUTZPGJ
-A KUBE-SEP-66Y2YBANTQJCS3YD -s 192.168.163.180/32 -m comment --comment "monitoring/prometheus-k8s:web" -j KUBE-MARK-MASQ
-A KUBE-SEP-66Y2YBANTQJCS3YD -p tcp -m comment --comment "monitoring/prometheus-k8s:web" -m recent --set --name KUBE-SEP-66Y2YBANTQJCS3YD --mask 255.255.255.255 --rsource -m tcp -j DNAT --to-destination 192.168.163.180:9090
-A KUBE-SEP-JAKCZKINWEKVQXB6 -s 192.168.163.181/32 -m comment --comment "monitoring/prometheus-k8s:web" -j KUBE-MARK-MASQ
-A KUBE-SEP-JAKCZKINWEKVQXB6 -p tcp -m comment --comment "monitoring/prometheus-k8s:web" -m recent --set --name KUBE-SEP-JAKCZKINWEKVQXB6 --mask 255.255.255.255 --rsource -m tcp -j DNAT --to-destination 192.168.163.181:9090
-A KUBE-SERVICES -d 10.106.193.17/32 -p tcp -m comment --comment "monitoring/prometheus-k8s:web cluster IP" -m tcp --dport 9090 -j KUBE-SVC-IFO32E4YIRUTZPGJ
-A KUBE-SVC-IFO32E4YIRUTZPGJ ! -s 192.168.0.0/16 -d 10.106.193.17/32 -p tcp -m comment --comment "monitoring/prometheus-k8s:web cluster IP" -m tcp --dport 9090 -j KUBE-MARK-MASQ
-A KUBE-SVC-IFO32E4YIRUTZPGJ -m comment --comment "monitoring/prometheus-k8s:web -> 192.168.163.180:9090" -m recent --rcheck --seconds 10800 --reap --name KUBE-SEP-66Y2YBANTQJCS3YD --mask 255.255.255.255 --rsource -j KUBE-SEP-66Y2YBANTQJCS3YD
-A KUBE-SVC-IFO32E4YIRUTZPGJ -m comment --comment "monitoring/prometheus-k8s:web -> 192.168.163.181:9090" -m recent --rcheck --seconds 10800 --reap --name KUBE-SEP-JAKCZKINWEKVQXB6 --mask 255.255.255.255 --rsource -j KUBE-SEP-JAKCZKINWEKVQXB6
-A KUBE-SVC-IFO32E4YIRUTZPGJ -m comment --comment "monitoring/prometheus-k8s:web -> 192.168.163.180:9090" -m statistic --mode random --probability 0.50000000000 -j KUBE-SEP-66Y2YBANTQJCS3YD
-A KUBE-SVC-IFO32E4YIRUTZPGJ -m comment --comment "monitoring/prometheus-k8s:web -> 192.168.163.181:9090" -j KUBE-SEP-JAKCZKINWEKVQXB61.2 找到具体规则
[root@TOS-1566 monitor]# iptables -L cali-pi-_NEUmkCPcORE5wvFnfMr -n --line-numbers
Chain cali-pi-_NEUmkCPcORE5wvFnfMr (2 references)
num target prot opt source destination
1 MARK tcp -- 0.0.0.0/0 0.0.0.0/0 /* cali:CjW10JzfBGI--RdM */ /* Policy monitoring/knp.default.prometheus-k8s ingress */ match-set cali40s:Y_WAIFZXBK4GNGes7ttP63u src multiport dports 8080,9090 MARK or 0x10000
2 RETURN all -- 0.0.0.0/0 0.0.0.0/0 /* cali:DKdxI3U_nSOSkdjr */ mark match 0x10000/0x10000
3 MARK tcp -- 0.0.0.0/0 0.0.0.0/0 /* cali:YLuP8_-FuuF7UZpq */ match-set cali40s:kyUh-Brv3zHPsq8RxXXVOCs src multiport dports 9090 MARK or 0x10000
4 RETURN all -- 0.0.0.0/0 0.0.0.0/0 /* cali:yux-UPSIi55LIGcG */ mark match 0x10000/0x10000
5 MARK tcp -- 0.0.0.0/0 0.0.0.0/0 /* cali:cMbHqB8WfU6d9fRO */ match-set cali40s:s49yZV9WMLGmTGGY2hWGVOR src multiport dports 9090 MARK or 0x10000
6 RETURN all -- 0.0.0.0/0 0.0.0.0/0 /* cali:2o3_fpBZRdo0BstG */ mark match 0x10000/0x10000你现在看到的
cali-pi-_NEUmkCPcORE5wvFnfMr规则,其实是 Calico NetworkPolicy 的“编译产物”,不是直接写 IP + DROP/ACCEPT 那种裸规则,而是通过 ipset + mark + RETURN 来间接控制流量的。
1.3 看到具体控制
Calico 的实现思路是:
- ipset 保存 NetworkPolicy 中允许的源/目的 Pod 的 IP 列表
- 比如
match-set cali40s:Y_WAIFZXBK4GNGes7ttP63u src表示源 IP 在某个 ipset 里(这一组就是被允许访问 8080/9090 的 Pod IP)。- 命中规则时,MARK or 0x10000 给这个包打一个 mark。
- 接着匹配
mark match 0x10000/0x10000→RETURN(允许流量继续走后面的 ACCEPT)。- 没有匹配的包,最终会在默认链(例如
cali-pi-DEFAULT)被 DROP。所以它不直接写 “ACCEPT 192.168.x.x”,而是:
ipset match → 打标记 → RETURN(允许) 没匹配 → 最后 DROP
# prometheus 服务IP
[root@TOS-1566 monitor]# ipset list cali40s:Y_WAIFZXBK4GNGes7ttP63u
Name: cali40s:Y_WAIFZXBK4GNGes7ttP63u
Type: hash:net
Revision: 7
Header: family inet hashsize 1024 maxelem 1048576 bucketsize 12 initval 0x493ea720
Size in memory: 568
References: 6
Number of entries: 2
Members:
192.168.163.180
192.168.163.181
# prometheus
[root@TOS-1566 monitor]# ipset list cali40s:kyUh-Brv3zHPsq8RxXXVOCs
Name: cali40s:kyUh-Brv3zHPsq8RxXXVOCs
Type: hash:net
Revision: 7
Header: family inet hashsize 1024 maxelem 1048576 bucketsize 12 initval 0x44310354
Size in memory: 568
References: 1
Number of entries: 2
Members:
192.168.163.176
192.168.163.177
[root@TOS-1566 monitor]# ipset list cali40s:s49yZV9WMLGmTGGY2hWGVOR
Name: cali40s:s49yZV9WMLGmTGGY2hWGVOR
Type: hash:net
Revision: 7
Header: family inet hashsize 1024 maxelem 1048576 bucketsize 12 initval 0x78f012de
Size in memory: 520
References: 1
Number of entries: 1
Members:
192.168.163.175只允许如下服务访问,从而导致Nodepode无法正常使用
正文完